Protect your company's endpoints (Workstations, laptops, virtual machines and Windows Servers) in a whole new way. Nothing runs without the user's knowledge. This is a next-generation malware defense. Designed to fill the blind spots left by conventional antivirus. A somewhat new approach: not merely reacting to threats, but nullifying their impact before they even activate. Even a state-sponsored cyberattack is intercepted and stopped in real-time at the first compromised endpoint in this implementation's Zero Trust mode. This solution not only block malware. It renders malwares irrelevant. And has been specifically developed to assist malware analysts and enhance the operational capabilities of Security Operations Centers (SOC) across TIER 1 to TIER 3 levels.
Currently supported versions: Windows 10 22H2 - Windows 11 25H2 (x64)
Full size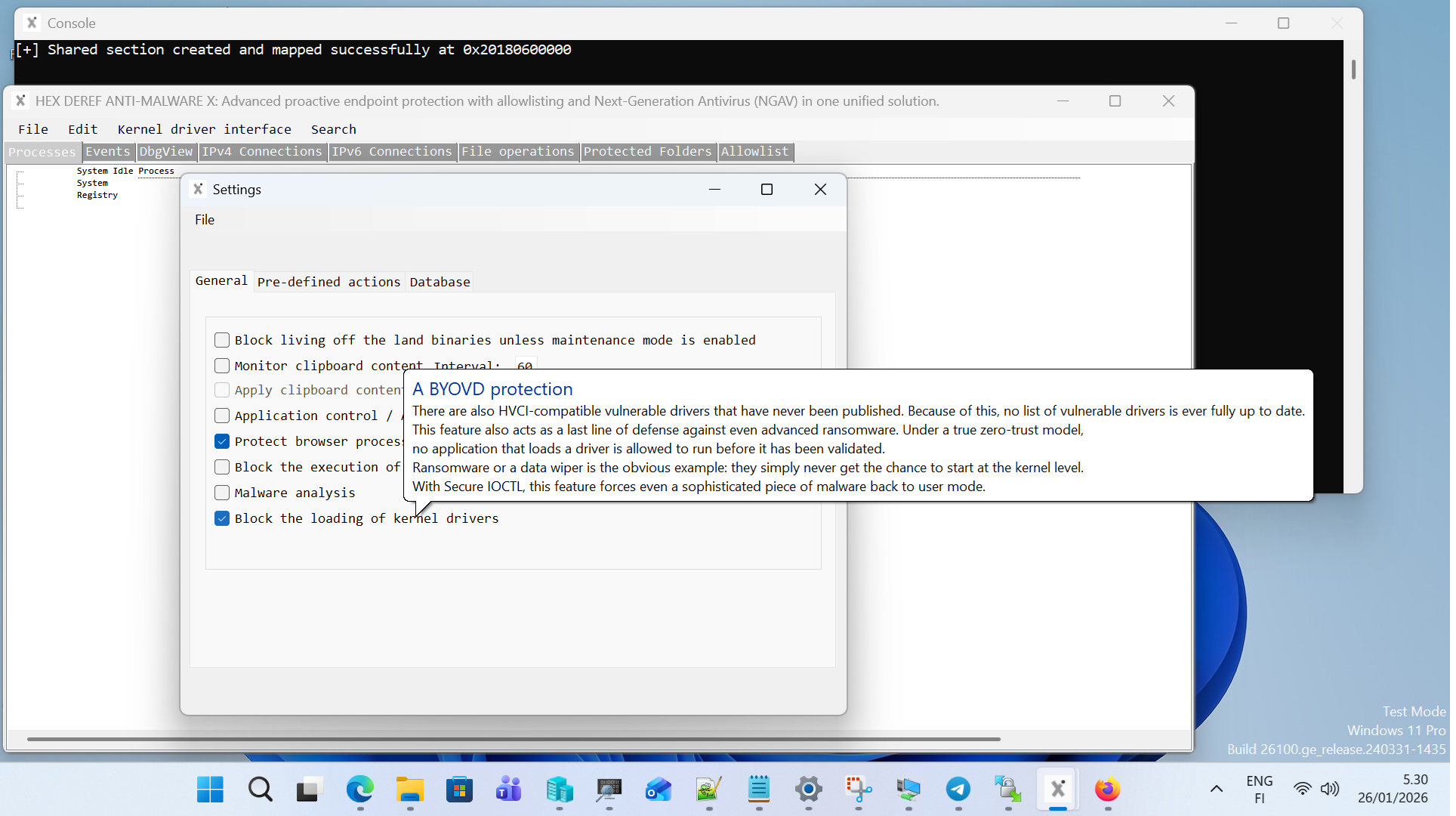
Malware may be deployed through remote access using credentials exposed in a breach, insider-launched malware, an undisclosed 0-day vulnerability (CVE-2025-53770), or triggered accidentally by an employee without malicious intent.
When a ransomware attack is launched, endpoint protection that cannot respond to these attacks in real time is, in this situation, is about as useful as having no protection at all. A malware backed by a state actor will, of course, reboot the device, effectively rendering the efforts of the cyberattack investigation team arriving on site almost entirely useless. Detection-based security does not recognize nor protect against unknowns, including new malware. Unknowns are only discovered and addressed by legacy detection-response (EDR) endpoint security providers once it has done damage to their clients.
Full size
Should the threat actor’s mission be to discreetly extract all data valuable for industrial espionage, the applications will not execute due to being absent from the allowlist. This action instantly generates a real-time alert, and the device is immediately isolated from the network as a precautionary measure.
This kind of malware deletes the logs and then renders the device unbootable. In such a situation, the only effective solution is the zero-trust concept. That means no unknown code — including digitally signed code — is executed within the company until a designated person has tested and verified it as safe.
By intercepting all unknown code at the kernel level in real time, these attack vectors are neutralized — eliminating both risk and reputational damage. This approach is particularly suited for small businesses (SMBs) lacking the budget for comprehensive round-the-clock SOC services.
Additional features includes advanced malware analysis and memory forensics. In malware analysis mode, hardly any threat goes undetected. This implementation corners the malware in its analysis mode and forces it to reveal itself. The anomaly detection feature preemptively blocks the execution of the process and flags it for manual analysis. As proactive measures, it can capture a real-time memory dump from both kernel and user space.
If your organization mostly uses Microsoft software or just a few other sofwares. This is the perfect solution. Simplicity is key. Nothing runs without an approval. The designated person or team adds them to the allowed list in Zero Trust mode. With the Home Edition, you stay in control — only the programs you approve can run. Nothing happens behind your back, ensuring complete transparency and peace of mind.
Proactivity refers to the ability to respond when an anomaly is detected on a device. In the example case, unknown code is executed on a device — code that has never previously run on any company system. The solution then performs a predefined action. For instance, as a precautionary measure, take a memory dump from the device or isolate it from the network.
Real-time threat prevention in code-signed malware that exploits previously undisclosed zero-day vulnerabilities
Malware signed with a legitimate and valid code signing certificate poses a unique challenge because it can appear trustworthy to endpoint protection systems. These threats must not be allowed to execute until they are explicitly verified as safe. In practice, only a zero-trust mode can block such state-sponsored threats in real time. Zero-trust architecture treats all code — even signed — as untrusted until proven safe. HEX DEREF X adds a critical layer of proactivity by checking whether the same code is running on any other device within the organization. This cross-device awareness helps detect lateral movement and coordinated attacks. It enables early containment before malware spreads across the network. The solution doesn’t rely solely on signature validation — it monitors behavior and presence. Zero-day vulnerabilities are flaws unknown to the vendor and unpatched at the time of attack.
The superficial protection offered by tradional antivirus solutions
Every day, countless new malware variants are engineered to steal sensitive data. Traditional antivirus (AV) solutions simply can't keep up, since every new malware variant requires a manual analysis and separate signature to be created offering no meaningful protection against these evolving threats. These solutions are hopelessly outdated, offering only superficial protection. Users are essentially just being charged for them without real value.
A dozen new malware variants per day. Even if they could analyze each one immediately as it appears. So despite their efforts, detection is so significantly delayed that it offers little to no practical benefit.
A Next-Generation Antivirus (NGAV) differentiates itself from traditional methods by detecting a previously unseen threats as anomalies, and through behavioral analysis without relying on static signature-based detection.
In addition to the Zero-Trust concept, the solution offers a mode more suitable for home users, where all unknown code (specifically code without a digital signature is automatically blocked unless explicitly approved). This approach proactively eliminates most threats by design.
The authors tests indicate that certain antivirus solutions perform actions without user consent — raising serious questions about trust, transparency, and privacy. When protection is only surface-level and sensitive data is collected regardless of user settings, it's time to re-evaluate what 'security' truly means.
The articles written by malware analysts from a certain antivirus solution were impressive. However, based on my preliminary tests, these features were not actually implemented in the product itself at a practical level. In other words, the articles are solid and the reverse engineers clearly know what they're doing — but why are these capabilities missing from the product being sold? The protection offered by the product is nowhere near the level suggested by the articles. Based on this, I’d say they’re knowingly selling something that only vaguely resembles real protection...
An antivirus solution or endpoint protection software collects all sensitive data, including browser history and file history (such as file names, sizes, and SHA-256 hash values). If a browser plugin captures POST data, even user credentials may be directly transmitted to its servers along with the URL. If a username has spread to the dark web following a data breach, an antivirus solution cannot alert the user unless it actively collects and monitors such credentials. It's worth keeping in mind: endpoint protection for which you don't have the source code can, in fact, already be or could at any time become spyware without the user's knowledge. That's why the source code for this solution is available for purchase as custom software development, leaving nothing to guesswork. Today, free antivirus software doesn’t truly exist. It often leverages the data it collects for commercial gain. Even file names alone can expose trade secrets or enable industrial espionage.
A new standard: No malware, just verified execution (Zero Trust)
That’s why this solution goes further: It doesn’t trust certificates. It trusts processes. Every executable must be explicitly approved by designated personnel. No implicit trust. No shortcuts. No assumptions. This isn’t about chasing signatures or reacting to threats. It’s about prevention by design. The author’s solution doesn’t just block malware — it makes its existence irrelevant. We’re not just talking theory — stolen code-signing certificates from data breaches or acquired under false pretenses are actively being used to sign malware, giving it a false sense of legitimacy. In these cases, even traditional Zero Trust implementations can be bypassed if they rely solely on certificate validation.
In zero-trust mode, ransomware has virtually no room to operate, as it simply won't run — whether digitally signed or not. An attacker cannot disable real-time protection on the device without being noticed, even if they gain remote access using compromised credentials. When it comes to IsaacWiper malware’s capabilities, even a single second of exposure is too much. That’s why the author solution stops threats instantly — at the kernel level, in real time, 24/7/365, operating in a zero-trust mode. The solution doesn’t replace your SOC — it empowers it. And for small and mid-sized businesses, it’s the most cost-effective protection on the market.
The attack techniques referenced in the accompanying article CVE-2025-8088 have been evaluated against the current implementation of the solution operating in zero-trust mode. Based on the authors analysis, these techniques are ineffective under this configuration. It is important to note that the volume and diversity of potential attack vectors continue to grow, particularly in cases involving undisclosed zero-day vulnerabilities within specific software applications. Such vulnerabilities, when not publicly disclosed, pose a significant challenge to proactive defense mechanisms and require continuous monitoring and adaptive security measures.
Even insider-originated threats trigger immediate scrutiny, and anomaly detection at the endpoint flags any deviation from normal behavior — including non-published zero-day exploits. These capabilities can be tailored as a custom software work to meet your company’s specific needs, thanks to a streamlined configuration model with only a handful of essential settings.
Case study
This simulates a real-life scenario in which an attacker has gained remote access to a company workstation using privileged administrator credentials. The attacker deploys a previously unpublished piece of malware designed for covert data exfiltration. The objective is to steal user credentials, source code, and any other valuable data that can be monetized on the dark web without the company’s awareness.
All malware variants designed to steal #1 steal #2 or wipe or encrypt data were automatically excluded from execution and subjected to manual analysis due to proactive security measures. When the Security Operations Center (SOC) conducted further testing, it quickly became evident that the file was ransomware — despite being digitally signed. This highlights the importance of layered defense and vigilant analysis.
The company emerged from the cyberattack unscathed. There were no disruptions to core operations, no reputational damage, and no need to deploy a CIRT team on-site. Sometimes a simple solution is better.
Advanced Application Control
The original developer’s implementation differs significantly from competitors in one key aspect: depending on the operating mode, either the device user defines which applications are allowed — at the process level or 'globally' based on digital signatures. Execution control is enforced by designated personnel — whether a SOC lead, security architect, malware analyst, or equivalent — who explicitly approve after manual analysis what is allowed to run. Any unrecognized or unauthorized activity is quarantined and subjected to manual analysis. Only after thorough review and validation is it permitted to execute, ensuring that proactive containment is driven by human oversight.
The moment a third party defines trusted applications on behalf of a company, the design has already fundamentally failed. For example, a program signed with a certificate obtained under false pretenses, or a previously approved application that turns malicious. Naturally, the purchasing company or educational institute must have the ability to remove items from the allowlist 24/7/365. If for no other reason, simply because the software may no longer be in use within the organization.
It’s worth noting that processes or DLL's can be added individually to the allowlist or based on the certificate signer.
Malware analysis
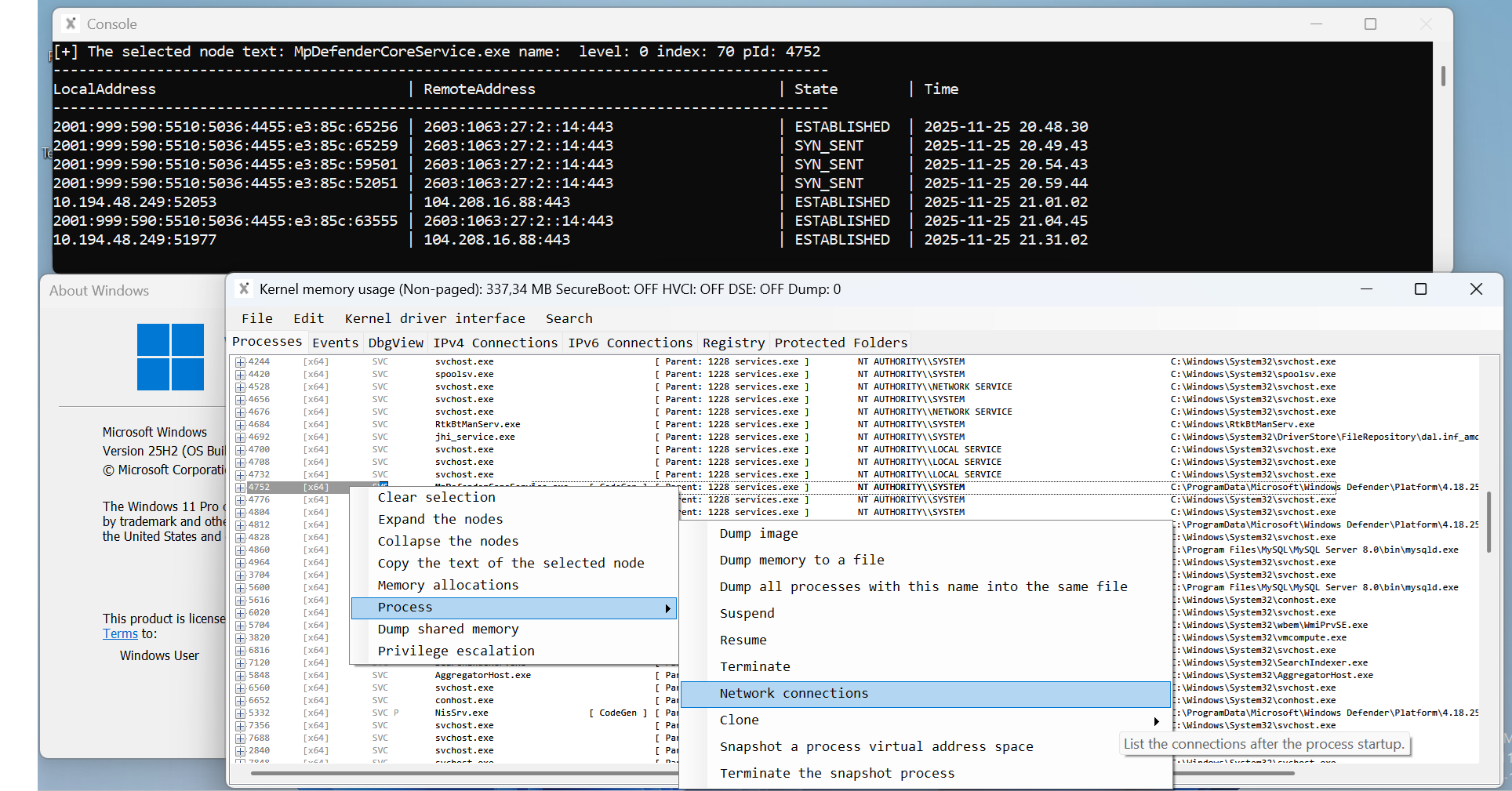
- Displays all running processes and their network connections that are not on the approved list (By default, all Microsoft-signed applications are automatically whitelisted)
- Ensures that unauthorized or suspicious software cannot operate undetected
- Empowers CIRT teams during on-site investigations to instantly identify potential malware or anomalous activity
- The system lists only newly initiated processes and their corresponding network connections, allowing immediate visibility into potential command-and-control (C2) communications
- The solution logs all processes along with their command lines and network connections into the database. This supports the investigation of potential data breaches and malware analysis
- Even without malware analysis mode activated, this solution enables post-incident verification to determine whether your company was exposed to a potential data breach
- Your malware analysts are as good as the softwares they use
In certain scenarios, a straightforward approach can outperform complex AI-driven solutions.
What can the on-site CIRT team can do if the malware securely removes itself from the device and restarts it? Not much except send the invoice. If this solution is running in zero-trust mode, you won’t need them anyway, because the attack stops at the first compromised device.
If a cyberattack does occur, and backups have been restored, but the root cause remains unknown, this kind of cyber threat mitigation solution needs to be deployed on the device in order to determine the root cause. Moreover, this kind of system is well-suited for hunting new threats. With this solution, you minimize or completely prevent the following effects: financial losses, reputational damage, operational disruptions caused by malware — and regulatory fines under frameworks like NIS2.
Key features (No comparable solution with these features can be found through search engines):
- Zero Trust - In this security-enhanced mode, the system implements strict execution controls that block all code from running without the user’s deliberate initiation or explicit consent (excluding Microsoft-digitally-signed processes). Everything else is blocked by default and flagged as an anomaly for manual analysis. Not even an APT-level ransomware or spyware can cause any damage. Although a process or its digital signature may be whitelisted, its behavior is continuously monitored to detect any potential malicious activity that may emerge over time
- Advanced process protection: Processes can be protected at the kernel level based on their digital signature, ensuring: Process memory cannot be read or written from user space. Protected processes are immune to code injection. By configuring the settings, browser processes can be secured in such a way that even fileless malware cannot hide within them. Most importantly, it prevents the extraction of user credentials or other sensitive information from browser memory
- The attack surface is minimized to a near-zero level
- Anomaly detection flags any deviation. Zero-day threats are neutralized before they can act — because they’re not on the allowlist
- Advanced malware analysis and memory forensics
- Designed to accelerate root cause analysis, the solution enables rapid identification and resolution of system anomalies, minimizing downtime and enhancing operational resilience
- Kernel physical memory scanner
- User-mode memory scanner, including WinTcb protected processes
- Secure IOCTL communication (The Exploitation #1 and Exploitation #2 mentioned in the article is not possible with this protection)
- A Next Generation Anti-Virus (NGAV) goes beyond traditional antivirus solutions – no signature updates, no reboots, and operates seamlessly even offline
- The solution runs alongside existing endpoint protections and kernel-level anti-cheats, while also providing deep visibility into their behavior
- Proactive nature - After detecting an anomaly, it can automatically capture a memory dump from kernel memory or user-space memory based on predefined actions or isolate the device from the network where the anomaly was detected. This enables an immediate forensic analysis without requiring on-site teams
- Always-on, real-time defense at the kernel level because threats never sleep
- Protected Folders (ransomware and data theft protection)
The solution logs all processes along with their command lines and network connections into the database. This supports the investigation of potential data breaches and malware analysis.
The allowed applications list is maintained by the device user. This can be tailored through software development to suit your organization’s requirements.
The user interface (UI) has been coded with C# .NET 8.0 so that the project would be easier to customize and be more easily modifiable.
This solution does not require or use any third-party additional protection layers. Therefore, the kernel driver is stable, and the source code is maintainable and well-documented.
Advanced memory scanner
Detects and exposes all processes (including CodeGen protected) accessing user credentials in real time. Instantly flags any activity involving the exfiltration of sensitive data. You’ll be astonished by what it uncovers — threats you didn’t even know existed.
Unauthorized credential access by antivirus or endpoint protection software or kernel-level anti-cheat? This solution ensures it’s detected — no exceptions. No search engine reveals a memory scanner like this — there’s nothing remotely similar to compare results with.
Availability of the source code
The user interface (UI) is written in C# .NET 8.0. The kernel driver is written in C/C++. The source code is available for purchase as a software work non-exclusively without resale rights for internal use within a company.
Total transparency: Review, audit, and adapt the code to meet your security standards. Brand freedom: Deploy under your own company name and visual identity. The original author offers a cybersecurity solution built on the principle that real trust begins with visibility.
Its worth to mention that even the most trusted endpoint protection can, under the guise of its features, perform spyware-like operations at any time without the knowledge of the company or the device user. One such feature is scanning all files. Based solely on file names, and depending on a company’s naming conventions. It’s often easy to tell what kind of data to extract. At some point, you have to place your trust somewhere but source code leaves nothing to guesswork.
The origin of the source code must not be misrepresented. The original author of the source code is White Byte. The logo is the copyrighted creation of the original author and may not be used in any rebranded or derivative solutions without explicit permission.
The source code provides a solid foundation for developing kernel-level anti-cheat mechanisms on Windows with relative ease.

